...
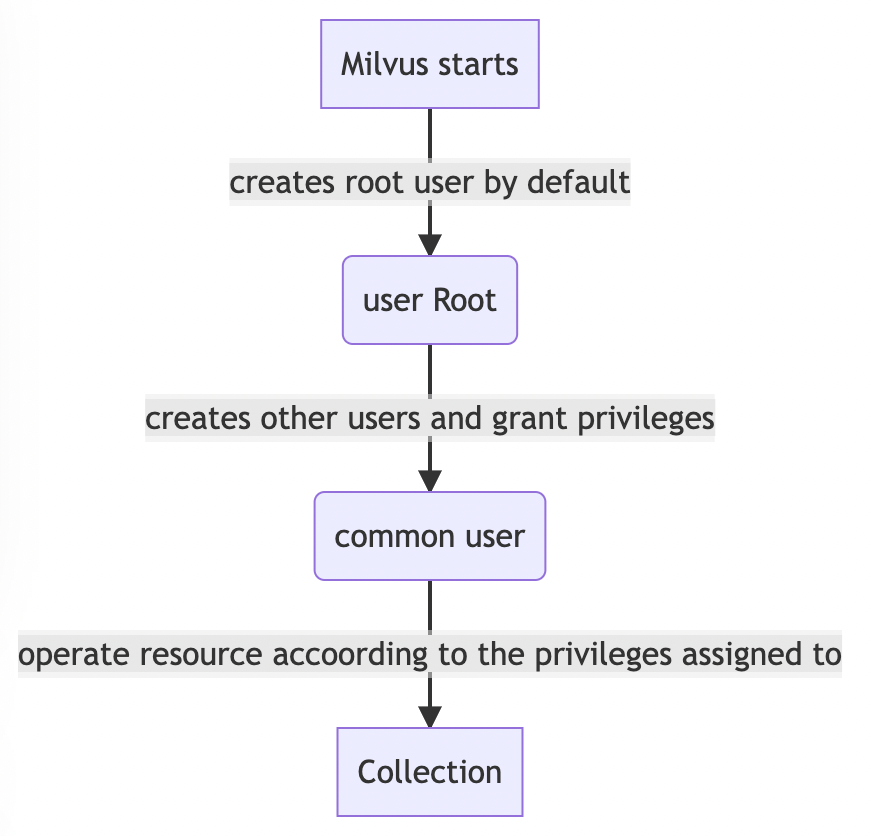
This project aims to support role-based access control. Users can do their operations according to the privileges assigned to them. And administrators of the Milvus cluster can manage users and operations under control.
Design Details
Entities
User: Every user has a unique identifier and is assigned a number of privileges.
...
2、Resource Types
id | resource_typeresource_name | created_time |
Resource types are globally unique, no need to add attribute tenant for it.
...
By design, a role inherited from another role is not possible here.
6、Privileges 6、Privilege grants of resource COLLECTION
id | tenant | grantor_name | principal_name | principal_type | collection_priv | collection_id | is_deleted | created_time |
Grantor_name is the user who grants the privileges.
Principal_name is the target which grantor grants privileges to.
The value of principal_type are USER or ROLE.
Collection_priv is the privilege to a collection, like SELECT, INSERT, UPDATE, etc.
For some collections which have alias, it will first get the real collection of the alias. Privilege verification will be based on the real collection not the alias. Collections stored in the table are also the real collection, not the alias.
The wildcard mode is supported for the collections in the table.
7、Privilege grants 7、Privileges of resource DATABASE (Not used since database is not supported in Milvus for now)
id | tenant | grantor_name | principal_name | principal_type | db_priv | db_id | is_deleted | created_time |
...
KV Store Schema
1、User
/prefix/credentialscredential/users/{tenant}/{username} | {"userTypek1": "v1", "k2": "adminv2"} |
2、Resource Types
/prefix/credentialscredential/resources/{resourcenameresourceType} | nil |
3、Privilege
/prefix/credentialscredential/privileges/{tenant}/{resourceType}/{privilege} | nil |
4、Role
/prefix/credentialscredential/roles/{tenant}/{rolename} | nil |
5、Role mapping
/prefix/credentialscredential/user-role-mapping/{tenant}/{username}/{rolename} | nil |
6、Grantee's Privileges6、Privilege Grants
/prefix/ |
credential/ |
privilege- |
grants/{tenant}/{principalType}/{principalName}/{resourceType}/{resourceName} | [{"resource":"SELECT", "grantor":"Alice"}, {"resource":"UPDATE", "grantor":"Bob"}] |
Resources & Privileges defined in Milvus
Users/Roles can be granted the following privileges:
| Privileges | Resources |
|---|---|
| ALL | Collection |
| CREATE | Collection |
| DROP | Collection |
| ALTER | Collection |
| READ | Collection |
| LOAD | Collection |
| RELEASE | Collection |
| COMPACT | Collection |
| INSERT | Collection |
| DELETE | Collection |
Index-related operations are included in ALTER privilege, like building, dropping index.
Default Roles
There are two default roles: admin, public.
Role admin have ALL the privilege. Role public only has READ and LOAD privileges.
APIs
For every API, parameter tenant is mandatory for avoiding loading too much data to memory.
...
Only root user can create roles. Role name cannot be "admin" or "public".
2、Grant & revoke privileges
...
| Code Block | ||
|---|---|---|
| ||
func GrantPrivilege(privilege string, resourceType string, resourceName string, principalName string, principalType string) bool func RevokePrivilege(privilege string, resourceType string, resourceName string, principalName string, principalType string) bool |
The user granting privileges must also have the privilege being granted on the target collection. For example, a user granting SELECT privilege on a collection to another user must have the GRANT and SELECT privileges on that table. There is no limitation for the root userOnly root user can grant & revoke privileges.
3、List grants for specific a user/role and resource
| Code Block | ||
|---|---|---|
| ||
func UserGrantListPrincipalGrantList(principalName string, principalType string, resourceType string, resourceName string) []UserGrantPrincipalGrant |
Output structure:
| PrincipalName | PrincipalType | Privilege | ResourceType | ResourceNamePrincipalName | |||
|---|---|---|---|---|---|---|---|
| Alice | PrincipalTypeUSER | PrivilegeINSERT | Collection | tbl_1 | Alice | User | INSERT |
Users can only query the grants for himself. And only root user can query grants for a role.
...
| Code Block | ||
|---|---|---|
| ||
func AddUserToRole(userName, roleName string) bool
func RemoveUserFromRole(userName, roleName string) bool |
Only root user can manipulate role membership.
...
Output:
| RoleName |
|---|
| admin |
| role_a |
Only root user can use the api.
8、List role memberships
| Code Block | ||
|---|---|---|
| ||
func RoleMembershipList(roleName string) []RoleMembership |
...
Only root user can use the api.
10、List roles of a user (useless???)
| Code Block | ||
|---|---|---|
| ||
func rolesOfUser(username string) []string |
...
The root user cannot be deleted.The root is initialized by default when milvus service starts. Once the root user is created, basic auth will be turned on automatically.
Other Notices
- Presetting There will be initialization program for presetting users, resource types, privileges are stored in local files. When milvus starts, it will load these files and insert records into database.Presetting users, resource types and privileges can be added into files and taking effect after restarting milvus service. Before the Milvus go to service, they are inserted into the meta table.
- The root user is the only user that has privileges for creating and dropping usersto create/drop/grant/revoke users and privileges.
- In MEP-27, basic auth is taking effect if there are any existing users. Since root user is created by default once Milvus service starts, it needs to will introduce a toggle to know where the basic auth indicate whether the authentication is turned on.
- Using Casbin for role-based privileges check ???.
Test Plan
Testing all the APIs listed above.
...