...
- At most ONE user can be created for a milvus instance.
- SDK clients MUST encrypt password when connecting to milvus service.
Authentication Workflow
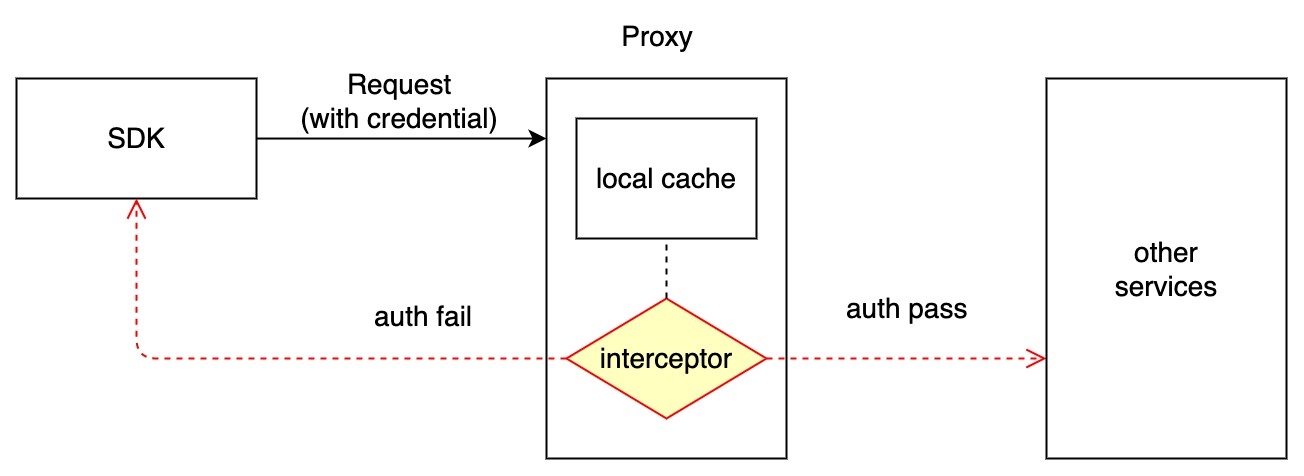
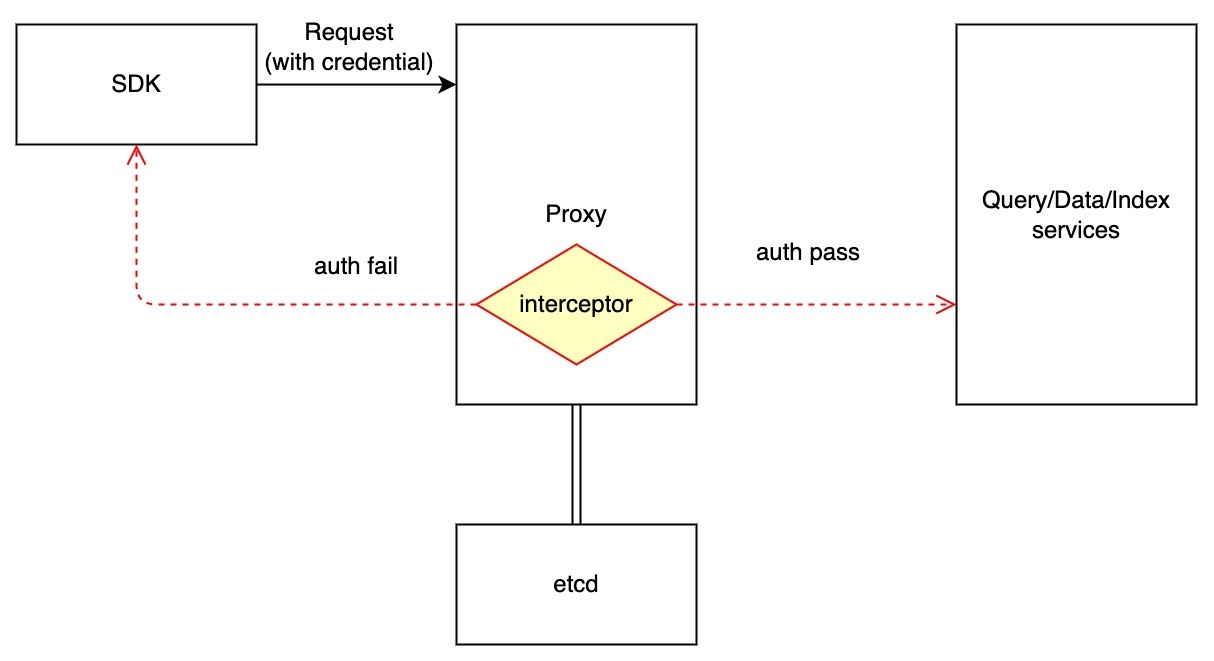
Since grpc requests all handled by proxy, we will do the authentication in the proxy component. Logging in to the milvus instance will follow the processes below:
- Create credential for each milvus instance and store encrypted password in etcd. Here we use package bcrypt for encrypting the password which implements Provos and Mazières's adaptive hashing algorithm.
- SDK client sends credential with password encrypted when connecting milvus service.
- Milvus proxy component intercepts the request and verify the credential.
- Credentials are cached locally on RootCoord component. When credentials changed, RootCoord will be notified and update the Proxy component.
Cache Update Workflow
1、Credential apis are provided by RootCoord.
2、Credential apis persist credentials on etcd (or other storage like mysql), and create task called CredTask for updating local caches in all proxy components.
3、CredTask will iterate all the proxy components, and call every proxy's rpc for updating the local cache until all of them are success.
4、Auth interceptor in proxy component will just search credential records from local cache.
Etcd model for credentials
| Panel |
|---|
Key: ${prefix}/credentials/users/${username} Value: {"password": ${encrypted_password}, ...} |
Interface for operating of credentials apis
| Code Block | ||
|---|---|---|
| ||
struct Credential {
username string,
password string
}
func NewCredential(cred Credential) (bool,error)
func ListUsers() []string
func UpdateCredential(cred Credential) (bool,error)
func DeleteCredential(username string) (bool,error) |
...