...
There is no basic security model for milvus instances currently. Users can access any milvus instance once they have the address by any milvus sdk.
This project aims to support basic authentication with username/password. Clients need to provide username and password when accessing the milvus instance.
Design Details
Prerequisite
- SDK clients MUST encrypt password when connecting to milvus service.
- Milvus create default user root as an initial user to create other users.
Authentication Workflow
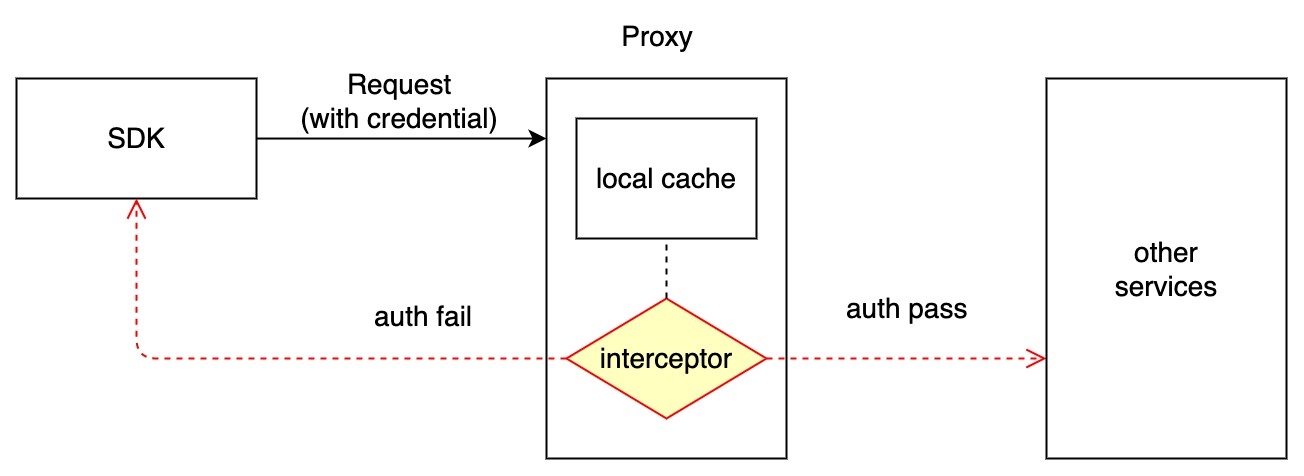
Since grpc requests all handled by proxy, we will do the authentication in the proxy component. Logging in on to the milvus instance will follow the processes below:
- Create credential for each milvus instance and store encrypted password in etcd. Here we use package bcrypt for encrypting the password which use bcrypt which implements Provos and Mazières's adaptive hashing algorithm.
- Client sends credential when connecting milvus instance.
- On the client side, SDK sends ciphertext when connecting milvus service. The ciphertext is base64(<username>:<passwd>) and attached to the metadata with the key "authorization".
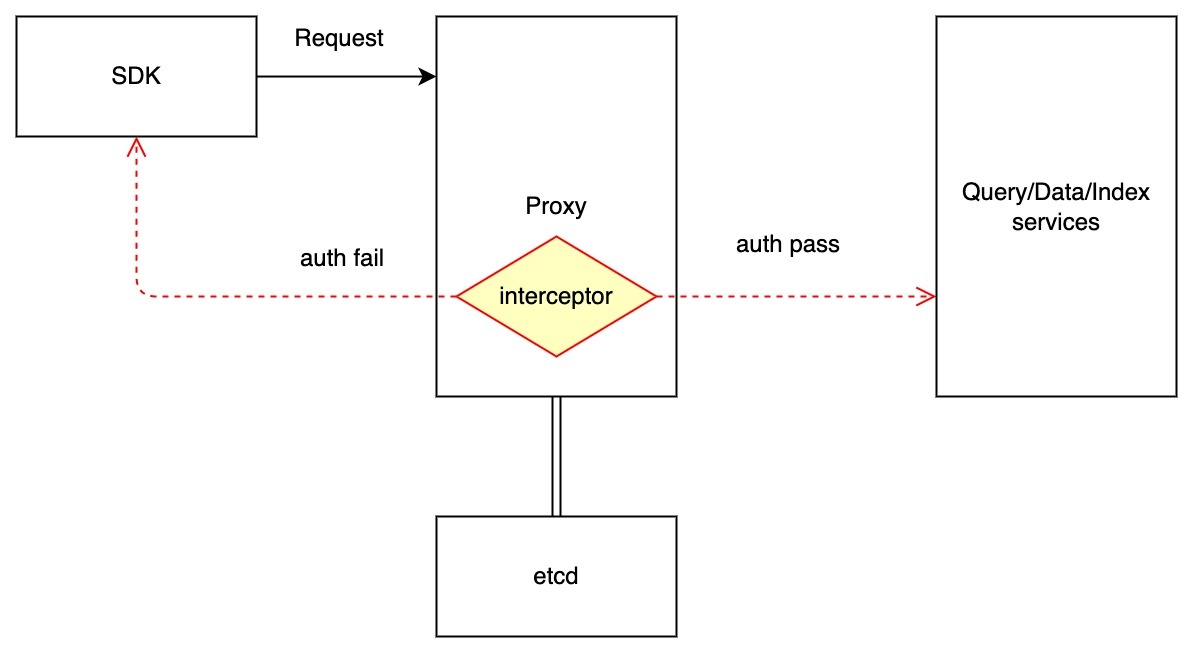
- Milvus proxy Proxy component intercepts the request and verify the credential.
- Credentials are cached locally on Proxy component.
Cache Update Workflow
- Credential apis (insert/query/delete credentials) are implemented by RootCoord.
- Credential modification apis persist credentials on etcd (or other storage like mysql), and call each proxy's api to invalidate local caches in all proxy components.
- Auth interceptor in proxy component will firstly find credential records from local cache. If the cache missed, it will trigger rpc call to fetch record from RootCoord and update the local cache.
Etcd model for credentials:
| Panel |
|---|
Key: ${prefix}/credentials/users/${username} Value: {"password": ${encrypted_password}, ...} |
Interface for operating of credentials :apis
| Code Block | ||
|---|---|---|
| ||
struct Credential {
username string,
password string
}
func NewCredential(cred Credential) (bool,error)
func ListCredentialListUsers() []Credential
func GetCredential(username string) *Credential
func UpdateCredential(cred Credential) (bool,error)
func DeleteCredential(username string) (bool,error) |
...
Compatibility
To be compatible with preview version, Milvus will use a toggle for it. If the toggle is on, it will check the credentials for each grpc call, otherwise it acts like the non-authenticate mode.
Test Plan
Case 1: create credentials for milvus
...
- Access without credentials should succeed
- Access with credentials should fail
...
- Access with correct certificates should succeed
- Access with incorrect certificates should fail
- Access without any certificates should fail
...
- should succeed (just ignore the input credential)
Future work
- Access without certificates should succeed
- Access with certificates should fail
...
SSL/TLS transportation
Authorization on RBAC control